本站启用https并针对性优化后,速度跟http相比仍不占优势,所以一并开启http2.0,nginx官网文档表明1.9.5及之后版本支持HTTP/2\(简称h2\)以取代spdy,使用nginx \-V可以查看ngx\_http\_v2\_module,不再有ngx\_http\_spdy\_module。
另外启用h2要求openssl版本不小于1.0.2,参见官方文档:<http://nginx.org/en/docs/http/ngx_http_v2_module.html>
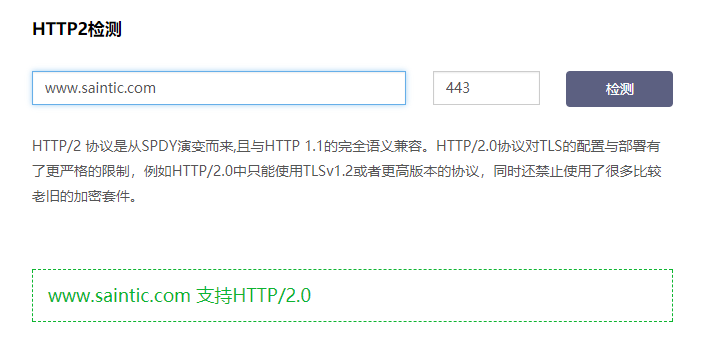
检测是否支持h2的在线网站:[myssl http2检测](https://myssl.com/http2_check.html)
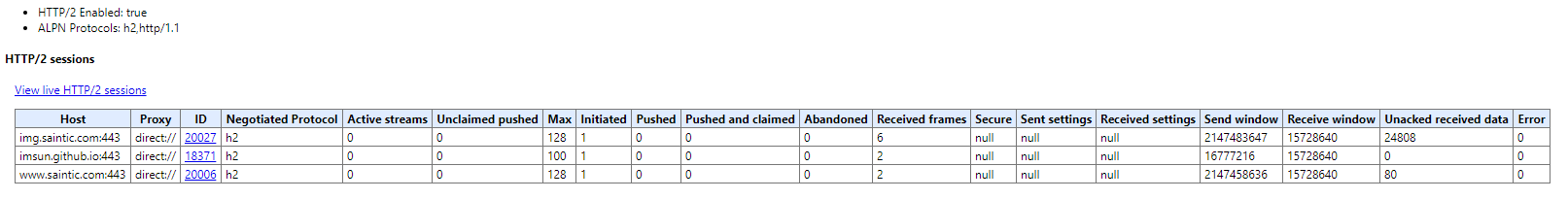
检测是否支持h2的chrome插件:[HTTP/2 and SPDY indicator](https://chrome.google.com/webstore/detail/mpbpobfflnpcgagjijhmgnchggcjblin)
#### 某个机器A
配置h2时,环境是:
nginx1.10.2(aliyun mirror), centos7.3, openssl忘记查看了~~
nginx -V如下(只保留有用部分):
nginx version: nginx/1.10.2
built by gcc 4.8.5 20150623 (Red Hat 4.8.5-4) (GCC)
built with OpenSSL 1.0.1e-fips 11 Feb 2013
TLS SNI support enabled
configure arguments: --prefix=/usr/share/nginx --with-http_ssl_module --with-http_v2_module
从结果看,nginx版本符合但openssl版本是1.0.1e不符合要求,遂升级nginx,部分输出结果:
Updated:
nginx.x86_64 1:1.12.2-1.el7
Dependency Updated:
nginx-all-modules.noarch 1:1.12.2-1.el7 nginx-filesystem.noarch 1:1.12.2-1.el7 nginx-mod-http-geoip.x86_64 1:1.12.2-1.el7 nginx-mod-http-image-filter.x86_64 1:1.12.2-1.el7 nginx-mod-http-perl.x86_64 1:1.12.2-1.el7 nginx-mod-http-xslt-filter.x86_64 1:1.12.2-1.el7
nginx-mod-mail.x86_64 1:1.12.2-1.el7 nginx-mod-stream.x86_64 1:1.12.2-1.el7
第二次从结果看并没有更新openssl,此时我才想起查看其版本:
# openssl version
OpenSSL 1.0.2k-fips 26 Jan 2017
# nginx -V
nginx version: nginx/1.12.2
built by gcc 4.8.5 20150623 (Red Hat 4.8.5-16) (GCC)
built with OpenSSL 1.0.2k-fips 26 Jan 2017
重启nginx后发现支持h2了,openssl版本也更新完毕,由于技术水平有限并不了解怎么更新的(依赖??)。
1. 在线检测
2. chrome插件(图标变成蓝色闪电形状即支持h2)
#### 某个机器B
这一个就淡定多了,nginx来自于官方yum源,操作前nginx -V结果是:
nginx version: nginx/1.10.1
built by gcc 4.8.5 20150623 (Red Hat 4.8.5-4) (GCC)
built with OpenSSL 1.0.1e-fips 11 Feb 2013
升级nginx输出部分:
Updated:
nginx.x86_64 1:1.12.2-1.el7_4.ngx
Dependency Updated:
openssl.x86_64 1:1.0.2k-8.el7 openssl-devel.x86_64 1:1.0.2k-8.el7 openssl-libs.x86_64 1:1.0.2k-8.el7
直接依赖更新了,更新后版本同机器A,万事大吉,今晚吃鸡。。。
结论:更新一下、重启一下,解决大部分问题。
#### 顺便贴一个https的配置:
server {
listen 80;
server_name your.domain.name;
charset utf-8;
access_log /var/log/nginx/access.log main;
rewrite ^/(.*)$ https://your.domain.name/$1 permanent;
}
server {
listen 443 http2;
server_name your.domain.name;
access_log /var/log/nginx/access.log main;
ssl on;
ssl_certificate xxxx;
ssl_certificate_key xxxx;
#OCSP Stapling开启,OCSP是用于在线查询证书吊销情况的服务,使用OCSP Stapling能将证书有效状态的信息缓存到服务器,提高TLS握手速度
ssl_stapling on;
#OCSP Stapling验证开启
ssl_stapling_verify on;
#OCSP Stapling的证书位置
ssl_trusted_certificate xxxx;
#用于查询OCSP服务器的DNS
resolver 8.8.8.8 114.114.114.114 valid=300s;
#查询域名超时时间
resolver_timeout 5s;
#SSL优化配置
#Session Cache,将Session缓存到服务器,这可能会占用更多的服务器资源
ssl_session_cache builtin:1000 shared:SSL:10m;
#开启浏览器的Session Ticket缓存
ssl_session_tickets on;
#SSL session过期时间
ssl_session_timeout 10m;
#只启用 TLS 系列协议
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
#加密套件,这里用了CloudFlare's Internet facing SSL cipher configuration
#完整参考 ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-RC4-SHA:ECDHE-RSA-RC4-SHA:ECDH-ECDSA-RC4-SHA:ECDH-RSA-RC4-SHA:ECDHE-RSA-AES256-SHA:RC4-SHA:HIGH:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!CBC:!EDH:!kEDH:!PSK:!SRP:!kECDH;
ssl_ciphers EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!aNULL:!MD5:!RC4:!DHE:!kEDH;
#由服务器协商最佳的加密算法
ssl_prefer_server_ciphers on;
#开启HSTS,并设置有效期为9460800秒(9个月),包括子域名(根据情况可删掉):includeSubdomains,预加载到浏览器缓存(根据情况可删掉)
add_header Strict-Transport-Security "max-age=15768001; preload";
#禁止被嵌入框架
#add_header X-Frame-Options DENY;
#防止在IE9、Chrome和Safari中的MIME类型混淆攻击
add_header X-Content-Type-Options nosniff;
#处理静态资源:
location ~ ^\/static\/.*$ {
root /xxxx;
}
location / {
proxy_pass http://xxx;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}